X (formerly Twitter) is experiencing its third major outage of the day, with users reporting widespread login and loading issues. The hacking group Dark Storm Team has reportedly claimed responsibility for a DDoS attack on the platform, according to a public Telegram post.
Newsweek has reached out to the X via email for comment on the matter.
What to know:
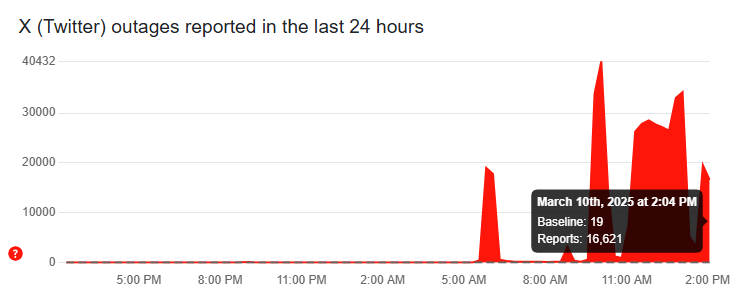
- More than 40,000 reports flooded Downdetector during the second outage.
- The current outage peaked at 29,143 reports and is now slightly declining.
- Dark Storm Team claims to have targeted X with a cyberattack.
- Users are unable to access the site, with many receiving error messages.
- This marks the third significant disruption to X’s service today.
Stay with Newsweek for updates on the latest X outage as the situation develops.
03:58 PM EDT The resurgence of the Dark Storm Team, a pro-Palestinian cyber group known for launching Distributed Denial of Service (DDoS) attacks, underscores the increasing cyber risks facing online platforms and critical infrastructure. Oded Vanunu, Chief Technologist for WEB 3.0 and Head of Product Vulnerability at Check Point Software, told Newsweek that the group’s reemergence signals potential service disruptions for users, including downtime and limited access to essential websites and apps.
“For businesses and organizations,” Vanunu said, “this reinforces the need for stronger cyber security defenses, especially against DDoS attacks, which can cripple online services. As these threats evolve, both users and companies should stay informed, have alternative communication channels, and be prepared for possible future disruptions.”
03:38 PM EDT Check Point’s 2025 Security report has raised alarming concerns over a 44% year-over-year increase in cyber-attacks, based on data from 170 countries, Check Point Research (CPR) told Newsweek in an email. The report highlights a significant shift in cyber warfare, with nation-states moving from isolated attacks to long-term, chronic campaigns aimed at eroding trust and destabilizing systems.
In February, U.S. organizations faced an average of 1,323 cyber-attacks per week, with the Media & Entertainment sector ranking as the fourth most targeted industry. This surge in cyber threats underscores the pressing need for prevention-first cybersecurity solutions.
“This breach is just the latest example of the importance of prevention-first cybersecurity solutions,” a CPR spokesperson told Newsweek.
03:14 PM EDT Check Point Research (CPR), a cyber threat research team, has told Newsweek that The Dark Storm Team, a pro-Palestinian cyberattack group known for launching Distributed Denial of Service (DDoS) attacks, has resurfaced after a period of inactivity. The group primarily targets Western entities, including those in the United States, Ukraine, the UAE, and Israel.
Over the past month, the Dark Storm Team has successfully attacked critical infrastructure, including Los Angeles International Airport (LAX), Haifa Port in Israel, and the UAE’s Ministry of Defense. In a statement, CPR highlighted the group’s role in destabilizing digital platforms, including the recent assault on X, underscoring the need for enhanced cybersecurity for social media platforms, which are vital to global communication.
CPR also noted that, in February, U.S. organizations faced an average of 1,323 cyberattacks per week, with the Media & Entertainment sector being the fourth most targeted.
03:02 PM EDT About 40 minutes after Elon Musk confirmed a “massive cyberattack” on X, the platform seems to be showing signs of recovery. While the service has been intermittent, particularly on the iOS app, it appears to be functioning better on the East Coast of the United States.
Though still slow to load, X is bouncing back, with DownDetector showing a drop in reported outages.
02:57 PM EDT Elon Musk, the billionaire owner of X, formerly Twitter, has said that he believes that today’s hack was an attempt to “silence” him.
In response to Musk’s post about the “massive cyberattack against 𝕏,” Hassan Sajwani posted that, “They want to silence you and this platform.”
“Yes,” Musk replied.
Musk had suggested earlier today that a “large, coordinated group and/or a country is involved” in the hack which took down the social media app on Monday.
“We get attacked every day, but this was done with a lot of resources. Either a large, coordinated group and/or a country is involved. Tracing …”
Yes
— Elon Musk (@elonmusk) March 10, 2025
02:47 PM EDT As the NFL’s legal tampering period began, fans were left frustrated as X (formerly Twitter) faced significant technical issues, hindering users from keeping up with the latest free agency moves. On Monday morning, the social media platform experienced widespread functionality problems, leaving fans uncertain about crucial player signings.
With big deals like Jimmy Garoppolo re-signing with the Rams and Chris Godwin’s extension with the Buccaneers, fans were left scrambling for updates. Some pundits turned to platforms like BlueSky and Threads to keep followers informed. The outage, which began around 9:45 a.m. ET, disrupted the flow of breaking news during a critical time for NFL fans.
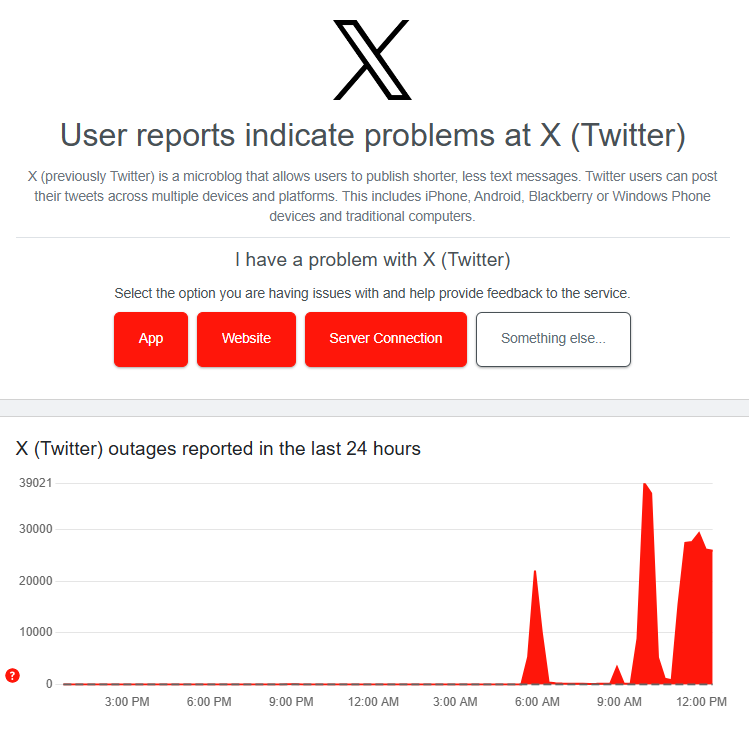
Screenshot from Downdetector showing that X is currently down. Screenshot from Downdetector showing that X is currently down. Screenshot/Downdetector
There are still over 16,000 reports of issues with X, formerly Twitter, on Downdetector.
02:16 PM EDT DDoS attacks are designed to overwhelm a target device or network, but different types target specific components of a network connection. To understand these attacks, it helps to know how a network connection is made, per Cloudflare.
A network connection on the Internet consists of several layers, which are described in the OSI model. This model is a conceptual framework with seven layers: application, presentation, session, transport, network, data link, and physical. Each layer has a different purpose in facilitating network communication.
While nearly all DDoS attacks involve flooding a target with traffic, they can be divided into three primary categories, with each targeting a different layer of the OSI model. Attackers may use one or more attack vectors, adjusting their methods in response to countermeasures taken by the target. This variation allows DDoS attackers to adapt their strategies, making these attacks more difficult to defend against.
01:57 PM EDT Today’s targeted hack on Elon Musk-owned X, comes after hundreds of protests have been held at Tesla dealerships and plants across the globe.
Activists are hoping to apply economic pressure against the world’s richest man who has had unparalleled influence in the Trump presidency and administration.
During a recent protest at a Tesla service and sales center on the outskirts of Louisville, Kentucky, demonstrators told Newsweek they were protesting Musk’s support for authoritarianism and far-right groups, and his apparent Nazi salute at a Trump inauguration event. Some expressed concern that Musk’s Department of Government Efficiency, or DOGE, was violating constitutional checks and balances by supplanting the role of Congress in spending decisions. Others called Musk a hypocrite for cutting federal services and jobs while his companies benefit from lucrative government contracts.
Private Tesla owners have also reported having their cars vandalized by protesters.
Protest organizer Hunt said his group will be back at the Louisville Tesla location again this coming weekend, and a website for the Take Down Tesla protests lists more than 100 upcoming demonstrations in the U.S., U.K., Portugal, Malaysia and Iceland.
“As the public sours on what Elon Musk is doing, we can actually do things that are effective to hurt his wealth and to stop what he’s doing,” Hunt said.
01:47 PM EDT Billionaire X, formerly Twitter, owner Elon Musk, believes that a “large, coordinated group and/or a country is involved” in the hack which took down the social media app on Monday.
Musk said that X got hack attempts on a daily basis but that this hack was different.
“There was (still is) a massive cyberattack against 𝕏,” he posted on X.
“We get attacked every day, but this was done with a lot of resources. Either a large, coordinated group and/or a country is involved. Tracing …”
There was (still is) a massive cyberattack against 𝕏. We get attacked every day, but this was done with a lot of resources. Either a large, coordinated group and/or a country is involved.
Tracing … https://t.co/aZSO1a92no
— Elon Musk (@elonmusk) March 10, 2025
01:21 PM EDT The numbers of people looking up X rival BlueSky have soared after Elon Musk’s social media app crashed repeatedly on Monday.
According to Google Trends, searches for BlueSky have more than doubled since the same time yesterday.
BlueSky started as a research initiative at what was then called Twitter in 2019 and became an independent company in 2021. Its development as as rival to X accelerated after Musk bought the app in 2022.
In 2023 it launched as an invite only service and then in February 2024, BlueSky opened its doors to the public.
It has grown swiftly with 30 million users recorded in January 2025.
01:09 PM EDT The hacking group Dark Storm Team has claimed responsibility for today’s hack on X, formerly Twitter.
The group is known for its sophisticated cyber warfare attacks and successful hacks of high-security systems.
According to Orange Cyberdefense, the group was formed in 2023 and has a pro-Palestinian focus.
Last month, the group vowed in a post to unleash a wave of cyberattacks on the government websites of NATO countries, Israel, and nations supporting Israel.
01:01 PM EDT The most obvious sign of a DDoS attack is when a website or service suddenly becomes slow or unavailable, according to Cloudflare. However, since other factors like a legitimate surge in traffic can cause similar issues, further investigation is often necessary. Traffic analytics tools can help identify signs of a DDoS attack.
Some telltale signs include suspicious traffic volumes coming from a single IP address or IP range, or a surge in traffic from users with similar behavioral profiles, such as the same device type or geolocation. An unexplained increase in requests to a particular page or endpoint is another red flag.
Additionally, odd traffic patterns, such as spikes at unusual times or frequent spikes at regular intervals (e.g., every 10 minutes), could indicate a DDoS attack in progress. While these are general indicators, more specific signs can vary depending on the attack’s nature.
01:00 PM EDT DDoS attacks are carried out using networks of internet-connected machines, often referred to as botnets. These botnets consist of computers and other devices, like IoT devices, that have been infected with malware, allowing an attacker to control them remotely. The individual infected devices are known as bots, and when grouped together, they form a botnet.
Once a botnet is established, the attacker can direct it to carry out an attack by sending remote instructions to each bot. In a typical DDoS attack, the bots send numerous requests to the target’s IP address, overwhelming its server or network. This can result in a denial of service, blocking legitimate traffic from accessing the service.
Since each bot is a legitimate internet device, distinguishing between attack traffic and regular user traffic can be extremely difficult, making DDoS attacks challenging to defend against.
12:56 PM EDT The hacking group Dark Storm Team has reportedly claimed responsibility for a DDoS attack on X. But what is a DDoS attack?
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network, as defined by Cloudflare, a network that helps websites and services run faster and more securely. This is done by overwhelming the target or its surrounding infrastructure with a flood of internet traffic, rendering it inaccessible to legitimate users.
DDoS attacks are effective because they use multiple compromised devices as sources of attack traffic. These devices can include computers, IoT devices, and other networked resources that have been exploited for the attack.
In simpler terms, a DDoS attack is like a traffic jam on a highway that prevents regular traffic from reaching its destination. The scale and severity of the attack depend on how many compromised devices are involved, making it a significant concern for online services and businesses.
Screenshot from Downdetector showing that X (FKA Twitter) is currently down, with a significant spike in outage reports on March 10, 2025. Screenshot from Downdetector showing that X (FKA Twitter) is currently down, with a significant spike in outage reports on March 10, 2025. Screenshot/Downdetector
There have been three outages involving X, formerly Twitter, on Monday.
Thousands of users have experienced issues logging onto the platform, with users mostly complaining of issues with the app at 57%, according to outage tracker Downdetector.